What’s changing
G Suite admins can now view and edit their users’ recovery information, such as backup email addresses and linked phone numbers. We also use this information to verify login requests and increase account security. By making sure your users have accurate and up-to-date information you can help make their accounts more secure.Who’s impacted
Admins only.Why you’d use it
This feature was developed based on customer feedback. Security and recovery information is important for many account verification processes, such as login challenge. To learn more about how adding recovery information can significantly increase the security of your account, see this blog post.Giving admins the ability to view and edit this information will mean they ensure more accounts have up-to-date recovery information, and increase the accuracy of the recovery information attached to G Suite accounts. This will help:
- Make it easier for users to access their account if locked out.
- Increase challenges and identification of suspicious login attempts to help to keep malicious actors out.
- Enable admins to provide direct support to users who are locked out of their account.
You can still add employee ID as a login challenge for extra security as well.
How to get started
- Admins: There are three ways admins can currently manage recovery information:
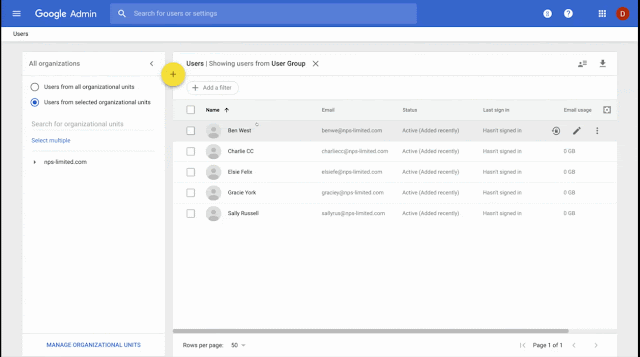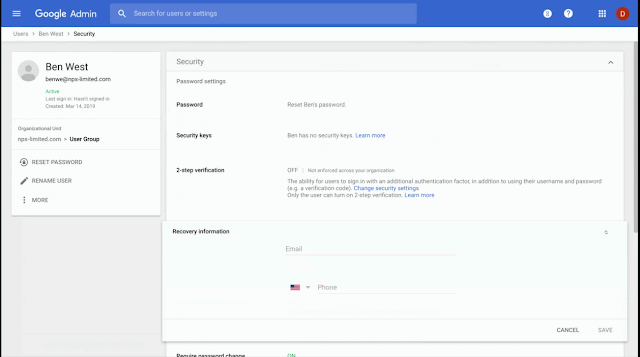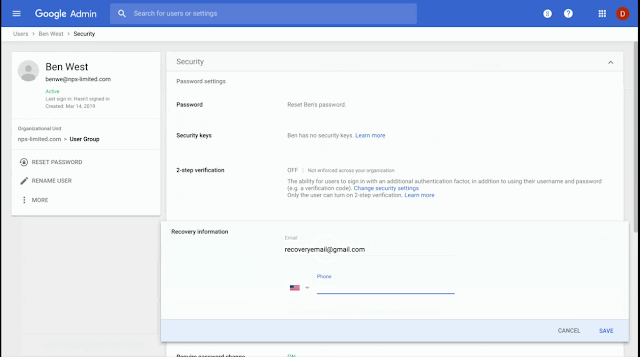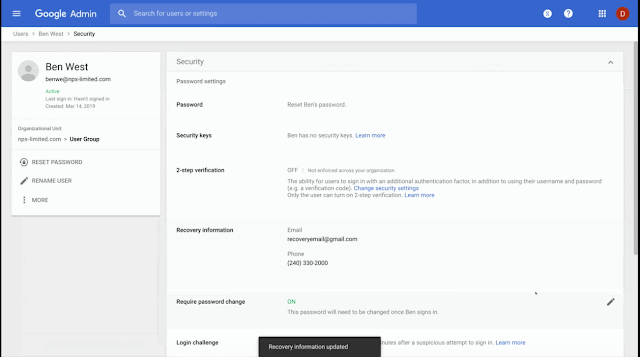
- Individual user accounts: Go to Admin Console > Users > Individual User > Security > Recovery information > Edit. You’ll be able to edit individual user recovery information directly.
- Bulk user upload tool (CSV): Use the bulk upload tool at Admin Console > Users to update in bulk. See the edit accounts with a spreadsheet section of this Help Center article for details.
- API: Use the Admin SDK Directory API.
- End users: No action needed, but can add recovery information by going to myaccount.google.com.
Helpful links
- Help Center: Add several users at once
- Admin SDK Directory API: Manage everything in your domain
- Google security blog: How effective is basic account hygiene at preventing hijacking
Availability
Rollout details- Rapid Release domains: Full rollout (1-3 days for feature visibility) starting on August 14, 2019
- Scheduled Release domains: Full rollout (1-3 days for feature visibility) starting on August 14, 2019
G Suite editions
Available to all G Suite editions.
On/off by default?
This feature will be ON by default.
Stay up to date with G Suite launches