Tag Archives: identity
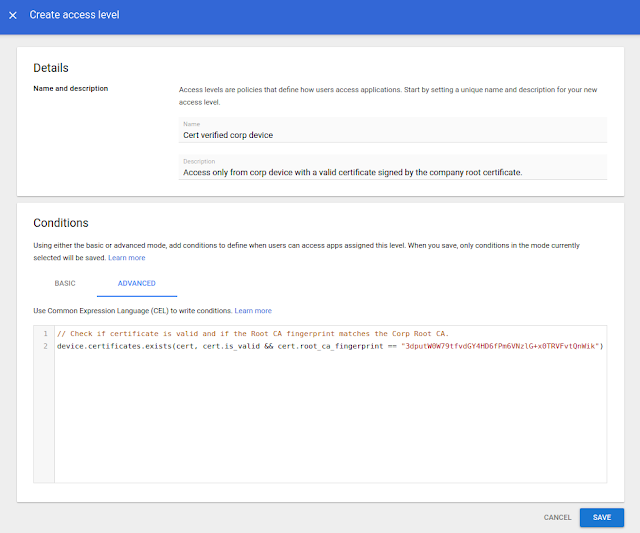
Use a new enterprise certificate condition to set context-aware access rules for company-managed devices
Quick launch summary
Getting started
- Admins: The feature is available by default, but needs to be configured before use. Use our Help Center to learn more about configuring enterprise certificates and configuring context-aware access rules.
- End users: No end user impact.
Rollout pace
- This feature is now available for all eligible users.
Availability
- Available to Google Workspace Enterprise Standard, Enterprise Plus, Education Standard, Education Plus, and Cloud Identity Premium customers
- Not available to Google Workspace Essentials, Business Starter, Business Standard, Business Plus, Enterprise Essentials, Education Fundamentals, Frontline, and Nonprofits, as well as G Suite Basic and Business, and Cloud Identity Free customers
Resources
Source: Google Workspace Updates
Making dynamic groups more powerful with custom user attributes and OrgUnit queries
What’s changing
- First, dynamic groups can now be defined by querying custom user attributes. This functionality is available as an open beta (no sign up required).
- Second, dynamic groups can also be defined based on users’ membership in Organizational Units (OUs). This feature is now generally available.
Who’s impacted
Why you’d use it
- Create a dynamic group for all users of a subsidiary (an organizational unit) based in a particular city or state.
- Create a dynamic group with all users with a custom attribute of a “job_skill” or “speciality”.
Getting started
- Admins: To take advantage of this new dynamic group functionality, you will need to have already defined custom user fields or organizational units.
- Once this is in place you can test membership queries and then create / update dynamic groups to take advantage of them.
- To query a customer attribute “EmployeeNumber” (based on this sample schema):
user.custom_schemas.employmentData.EmployeeNumber == '123456789' - To query all direct members of an organizational unit:
user.org_unit_id==orgUnitId('03ph8a2z1enx4lx') - To query all direct and indirect members of an organizational unit:
user.org_units.exists(org_unit, org_unit.org_unit_id==orgUnitId('03ph8a2z1khexns')) - End users: Not available to end users.
Rollout pace
- Custom user attribute queries are available now for all users in open beta (no sign up required)
- Organizational unit based dynamic group queries are now generally available for all users.
Availability
- Available to Google Workspace Enterprise Standard, Enterprise Plus, and Education Plus customers
- Not available to Google Workspace Essentials, Business Starter, Business Standard, Business Plus, Enterprise Essentials, Education Fundamentals, Frontline, and Nonprofits, as well as G Suite Basic and Business customers
Resources
Source: Google Workspace Updates
Set user language programmatically with the Directory API
Quick launch summary
Getting started
- Admins and developers: No action required. This function is available by default. Use our API documentation to learn more about using the Directory API to update the ULS.
- End users: No end user impact.
Rollout pace
- Rapid Release and Scheduled Release domains: Full rollout (1–3 days for feature visibility) starting on December 9, 2021.
Availability
- Available to all Google Workspace customers, as well as G Suite Basic and Business customers
Resources
Source: Google Workspace Updates
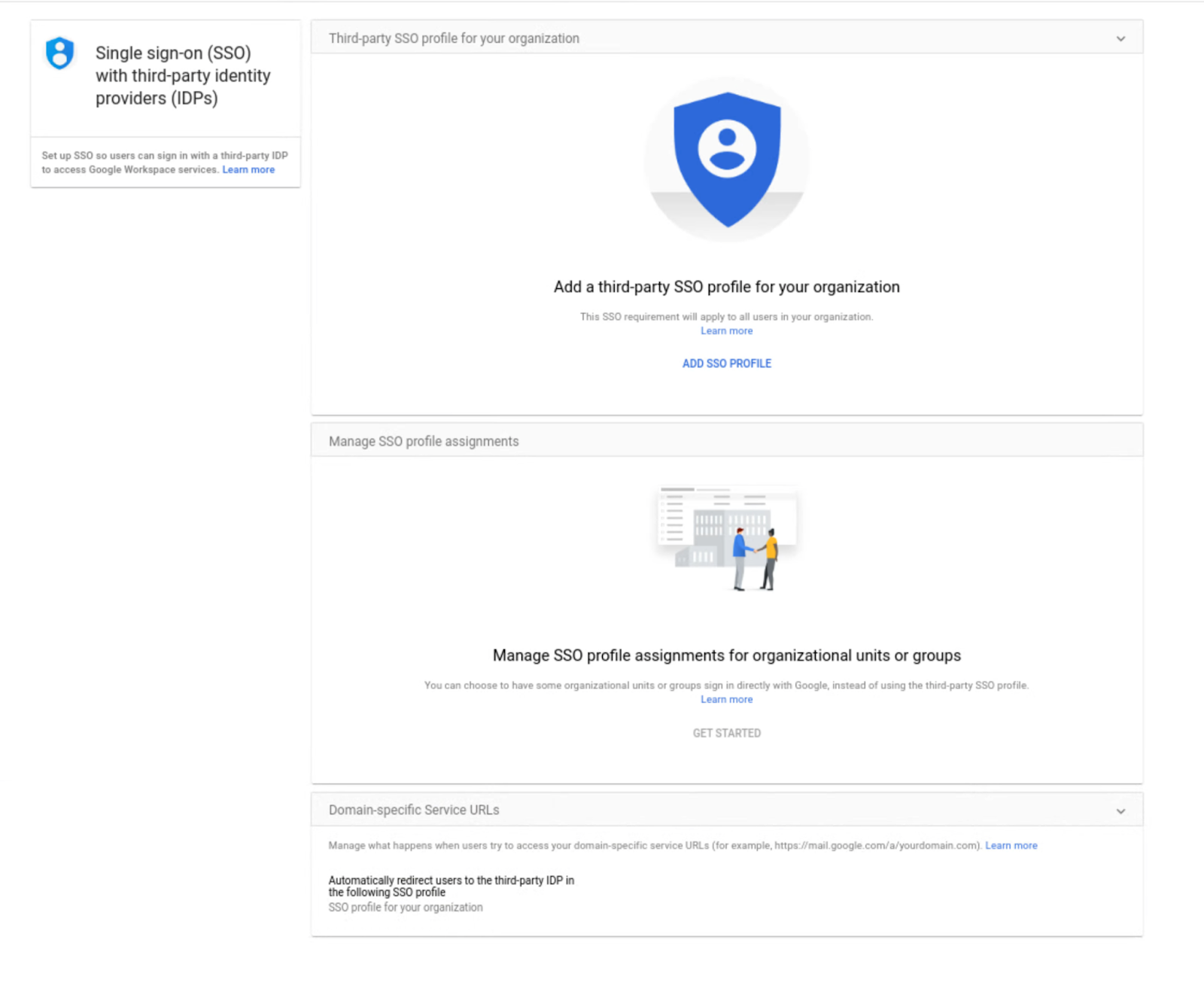
Assign SSO profile to organizational units or groups with the SAML Partial SSO feature, now generally available
What’s changing
Earlier this year, we announced a beta for assigning SSO profiles to organizational units or groups. This feature is now generally available and allows admins to specify groups or organizational units (OUs) to authenticate a subset of your users using Google.
Who’s impacted
Admins
Why it’s important
Currently, when you configure SSO with a third-party identity provider, the setting applies to your entire domain. However, there are some instances where you may want a subset of your users, such as vendors or contractors, to authenticate with Google instead. The Partial SSO feature gives you the flexibility to specify the authentication method for various users in your organization as needed.
Getting started
- Admins: In the Admin console, navigate to Security > Settings > Set up single sign-on (SSO) with a third party IdP > Manage SSO Profile assignments. Visit the Help Center to learn more about assigning SSO profiles to organizational units or groups.
- End users: No action required.
Rollout pace
- Rapid Release and Scheduled Release domains: Full rollout (1–3 days for feature visibility) starting on November 19, 2021
Availability
- Available to Google Workspace Business Starter, Business Standard, Business Plus, Enterprise Essentials, Enterprise Standard, Enterprise Plus, Education Fundamentals, Education Plus, Frontline, and Nonprofits, as well as G Suite Basic and Business customers
- Available to all Cloud Identity customers
- Not available to Google Workspace Essentials customers
Resources
Source: Google Workspace Updates
Control session length for Google Cloud Console and gcloud CLI now generally available
Quick Summary
- GCP Cloud Console
- gcloud command-line tool
- Any other application that requires Cloud admin scopes
Getting started
- Admins: This feature will be OFF by default and can be enabled at the OU level. You can find session length controls at Admin console > Security > Google session control. Visit the Help Center to learn more about how to set session length for Google Cloud services.
- End users: If a session ends, users will simply need to log in to their account again using the familiar Google login flow.
Rollout pace
- Rapid Release and Scheduled Release domains: Gradual rollout (up to 15 days for feature visibility) starting on October 18, 2021
Availability
- Available to all Google Workspace customers, as well as G Suite Basic and Business customers, and Google Cloud Identity Free and Premium customers
Resources
Source: Google Workspace Updates
Google OAuth incremental authorization improvement
Posted by Vikrant Rana, Product Manager, and Badi Azad, Group Product Manager
Summary
Google Identity strives to be the best stewards for Google Account users who entrust us to protect their data. At the same time, we want to help our developer community build apps that give users amazing experiences. Together, Google and developers can provide users three important ways to manage sharing their data:
- Give users control in deciding who has access to their account data
- Make it easier and safer for users to share their Google Account data with your app when they choose to do so
- Make it clear to users the specific data they are sharing with apps
What we are doing today
In service of that stewardship, today we are announcing an OAuth consent experience that simplifies how users can share data with apps. This experience also improves the consent conversion for apps that use incremental authorization, which requests only one scope. Users can now easily share this kind of request with a single tap.

Previous Screen New Screen
A quick recap
Let’s summarize a few past improvements so you have a full picture of the work we have been doing on the OAuth consent flow.
In mid-2019, we significantly overhauled the consent screen to give users fine-grained control over the account data they chose to share with a given app. In that flow, when an app requested access to multiple Google resources, the user would see one screen for each scope.
In July 2021, we consolidated these multiple-permission requests into a single screen, while still allowing granular data sharing control for users. Our change today represents a continuation of improvements on that experience.
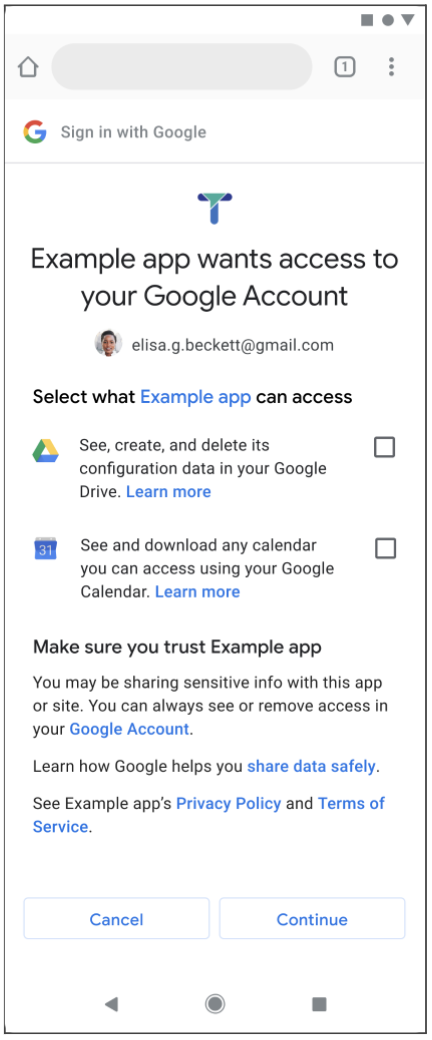
The Identity team will continue to gather feedback and further enhance the overall user experience around Google Identity Services and sharing account data.
What do developers need to do?
There is no change you need to make to your app. However, we recommend using incremental authorization and requesting only one resource at the time your app needs it. We believe that doing this will make your account data request more relevant to the user and therefore improve the consent conversion. Read more about incremental authorization in our developer guides.
If your app requires multiple resources at once, make sure it can handle partial consent gracefully and reduce its functionality appropriately as per the OAuth 2.0 policy.
Related content
Assign SSO profile to organizational units or groups with the new SAML Partial SSO beta
What’s changing
Who’s impacted
Why you’d use it
Getting started
- Admins: In the Admin console, navigate to Security > Settings > Set up single sign-on (SSO) with a third party iDP > Manage SSO Profile assignments. Visit the Help Center to learn more about assigning SSO profiles to organizational units or groups.
Rollout pace
- Rapid and Scheduled Release: Full rollout (1-3 days for feature availability) beginning on July 29, 2021
Availability
- Available to all Google Workspace and Cloud Identity customers
Resources
Source: Google Workspace Updates
Enhanced desktop security for Windows is now available for Google Workspace Business Plus customers
Quick launch summary
Google Workspace Business Plus customers can now manage and secure Windows devices through the Admin console, just as you do for Android, iOS, Chrome, and Jamboard devices. Now, Business Plus Admins can:
- Set Windows policies in the admin console which will ensure that all Windows 10 devices used to access Workspace are updated, secure, and within compliance of organizational policies.
- Perform admin actions, such as wiping a device and pushing device configuration updates, to Windows 10 devices from the cloud without connecting to corp network.
See our previous announcement for more details on the Windows 10 management features and benefits and the Help Center to learn more about enhanced desktop security for Windows.
Getting started
- Admins:
- Use our Help Center to learn how to enroll a device in Windows device management, how to enable enhanced desktop security for Windows, and how to manage Windows devices.
- Within Workspace and Cloud Identity, multiple devices per user can be managed at no additional cost.
Rollout pace
- This feature is available now.
Resources
- Google Workspace Admin Help: Overview: Google Credential Provider for Windows (GCPW)
- Google Workspace Admin Help: Manage Windows 10 devices
- Google Workspace Admin Help: Enhanced desktop security for Windows
- Cloud Blog: 6 new device, data, and user controls to help G Suite customers stay secure
Source: Google Workspace Updates
Apply context-aware access policies to mobile and desktop applications
What’s changing
Who’s impacted
Why it’s important
Getting started
- Admins: This feature will be OFF by default and can be enabled at the domain, OU, and group level when assigning an access level. Visit the Help Center to learn more about context-aware access, creating context-aware access levels, and assigning access levels to apps.
- End users: No action required.
Rollout pace
- Rapid Release and Scheduled Release domains: Gradual rollout (up to 15 days for feature visibility) starting on April 27, 2021